Introduction
The news is replete with reports of attackers exploiting web vulnerabilities to gain access to the private data of customers and clients that organizations have to be more proactive in protecting websites and applications. This is even more relevant when we consider the fact that companies rely on open-source software and packages to shorten their time to market.
While companies are usually in control of the packages and code they create from the start and therefore can decide their security strategies, using open-source packages and dependencies dilute the control they have since security vulnerabilities can creep into their applications.
The OWASP top ten list of vulnerabilities and how they affect your applications

The OWASP Foundation works to improve the security of software through its community-led open-source software projects, hundreds of chapters worldwide, tens of thousands of members, and by hosting local and global conferences. The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. They are globally recognized by developers and companies alike as the first step to building more secure applications. The last OWASP top ten list of security risks released in 2017 lists the following vulnerabilities as potential risks to any web application
- Injection.
- Broken Authentication.
- Sensitive Data Exposure.
- XML External Entities (XXE).
- Broken Access Control.
- Security Misconfiguration.
- Cross-Site Scripting XSS.
- Insecure Deserialisation.
- Using Components with Known Vulnerabilities.
- Insufficient Logging & Monitoring.
According to Wikipedia, the majority of web application attacks occur through cross-site scripting (XSS) and SQL injection attacks which typically are made possible by flawed coding and failure to sanitize application inputs and outputs. These attacks are ranked in the 2009 CWE/SANS Top 25 Most Dangerous Programming Errors.
During software development, with or without open-source dependencies, these ten vulnerability risks can potentially make applications and websites vulnerable to attack from hackers which can expose companies and organizations to various consequences including bankruptcy, lawsuit or even jail time.
Staying ahead of security vulnerabilities
To stay ahead of security vulnerabilities, companies must integrate security tools into the software development lifecycle (SDLC) that can assist teams in detecting vulnerabilities earlier in the development process when it is easier to address them. Firstly, they should be able to identify vulnerabilities and secondly, they should be able to fix these vulnerabilities. It is a mammoth task to keep track of all the lists of vulnerabilities identified and released daily and to then manually scan your entire codebase to identify and fix those vulnerabilities. That is why security-focused companies have provided tools that can seamlessly integrate into the SDLC and help teams identify and fix open source vulnerabilities.
Tools and Techniques
In this section, we will go through the various ways a company or software teams can identify and fix security vulnerabilities in their codebase and dependencies.
Using NPM (JavaScript)
NPM (node package manager) is a package manager that gives teams the ability to install and use open-source packages in their source code. NPM includes tools to help you audit the open-source dependencies you include in your project and rate the vulnerabilities risks from low to high. When installing packages, NPM automatically scans the dependencies and reports on the vulnerability risks. If there is any vulnerability in your dependency graph, you will see the report displayed in the image below.
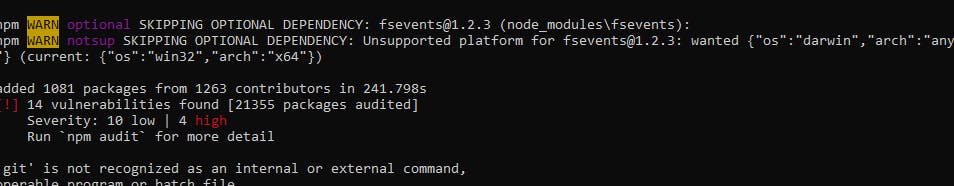
Running the command below will instruct NPM to attempt to fix all identified vulnerabilities.
npm audit --fix
NPM is limited in the vulnerabilities it can fix and also runs the risk of introducing new vulnerabilities to your project. Even at that, you still have to manually update and install the packages NPM recommends to fix the vulnerabilities. If you have a lot of dependencies to update, this could quickly result in a nightmare scenario. Some of these updates may result in breaking changes which means you have to take additional time to ensure that your project still works.
Enable vulnerability detection and monitoring on source-code hosting platforms
Some tools include integrations into popular repos - GitHub, BitBucket, and GitLab, and provide developer-focused security tools that operate within the native development environment, without compromising agility. For example, if GitHub detects a vulnerability from the GitHub Advisory Database or WhiteSource in one of the dependencies in a project’s repository's dependency graph, it sends the author a security alert. Additionally, Whitesource repo-integration goes beyond just providing an alert. It provides lots of features and advantages like getting real-time alerts and actionable insights on vulnerable open source libraries and dependencies within the repo UI, quick remediation with automatic pull requests that contain verified suggested fixes for vulnerable libraries and enforced and security policies with automated workflows that can track your repository and remediate vulnerabilities.
Using Renovate
Renovate is a free tool that runs continuously in the background and helps to automatically keep your dependencies up to date. It supports multiple languages and file types to detect dependencies wherever you use them. Renovate also runs your existing suite of tests on every update to avoid regression errors. Although it can’t detect specific vulnerabilities in your repo, it provides a way to keep all your libraries up-to-date which helps avoid the risk of introducing potential vulnerabilities.
Manually fixing the vulnerabilities
It is possible for teams to manually fix the vulnerabilities in their codebase when patches are released without introducing breaking changes in their project. This usually means installing an upgrade in your dependencies. Where the dependencies are no longer maintained, teams may have to take the responsibilities of investigating the vulnerability and creating a patch.
Benefits of using tools that integrate to your repository
Checkmarx lists the following as the benefits of using automated security tools:
- The security solution is integrated into the build automation tool. The application code can be scanned with each commit, making the results available almost instantaneously. It’s also possible to scan nightly builds with full system testing.
- Ability to halt the build when critical errors (medium/high) are detected. The biggest drawback with Manual Testing and other traditional security solutions mentioned in this article is the inability to find vulnerabilities on the go. They detect flaws at the latter stages of the sprints, creating numerous technical issues and maintenance complications. These problems are simply eliminated due to the practicality and flexibility of automated tools.
- Incorporate security findings into the daily Scrum meetings. If the security solution can help educate developers, it brings extra value. Static Code Analysis (SCA) findings can typically be exported for offline scrutiny and analysis.
- Improved ROI. The fixing of vulnerabilities early on also brings significant financial savings and benefits to the organization.
- Reduced friction between the security staff and the developers. With the automated solution built into the agile software development (ASD) process, all sides are actively involved in the security process.
Conclusion
Building software comes with risks of introducing potential software vulnerabilities. Although open-source packages reduce time to market, they, however, can expose projects and web applications to increased risks. It is possible to remediate those vulnerabilities manually, which at best, is a nightmare scenario. but Fortunately, developers now have tools at their disposal that automatically integrate into their repositories and do the heavy lifting of identifying and fixing security vulnerabilities.

